PowerShell Security Best Practices. Given that PowerShell cannot be disabled or removed from organizations that require it, the following actions are the recommended best practices to use PowerShell efficiently while preventing its use as an attack vector. Back in September 2017, I outlined some of the main themes surrounding PowerShell security. Familiarize yourself with PowerShell security best practices using the various links referenced below. Sign your scripts: Another method for keeping scripts Secure is by having them vetted and then signed, before importing them for usage. Don't store secrets (such as passwords) in PowerShell scripts and learn more about how to handle secrets. It would be nice to see an article on best practices for IT.administration. password security. User password security, while somewhat important, should never be a security concern if a network is built with security in mind from the get go. The issue of password security becomes truly significant when an IT team chooses not to implement a. Password security best practices in PowerShell According to the 2019 Data Breach Investigation Report by Verizon, stolen credentials are the major cause of data breaches. To safeguard passwords from cyberattacks like brute-force or password spray, compliance regulations like NIST define password security rules to ensure password complexity. Lab: Microsoft Security Workshop: Implementing Windows PowerShell Security Lab 1: Implementing Windows PowerShell Security Scenario. You manage an Active Directory environment with domain-joined Windows Server 2016 servers and Windows 10 Professional client computers.
Security
Always use PSCredential for credentials/passwords
You must avoid storing the password in a plain string object, or allowing the user to type them in as a parameter (where it might end up in the history or exposed to screen-scraper malware). The best method for this is to always deal with PSCredential objects (which store the Password in a SecureString).
More specifically, you should always take PSCredentials as a parameter (and never call Get-Credential within your function) to allow the user the opportunity to reuse credentials stored in a variable.
Password Best Practices Microsoft
Furthermore, you should use the Credential attribute as the built-in commands do, so if the user passes their user name (instead of a PSCredential object), they will be prompted for their password in a Windows secure dialog.
If you absolutely must pass a password in a plain string to a .Net API call or a third party library it is better to decrypt the credential as it is being passed instead of saving it in a variable.
Best Practice For Passwords
Other Secure Strings
Powershell Script Security Best Practices
For other strings that may be sensitive, use the SecureString type to protect the value of the string. Be sure to always provide an example for the user of passing the value using Read-Host -AsSecureString.
Note, if you ever need to turn a SecureString into a string, you can use this method, but make sure to call ZeroFreeBSTR to avoid a memory leak:
Powershell Password Security Best Practices Software

Powershell Best Practice
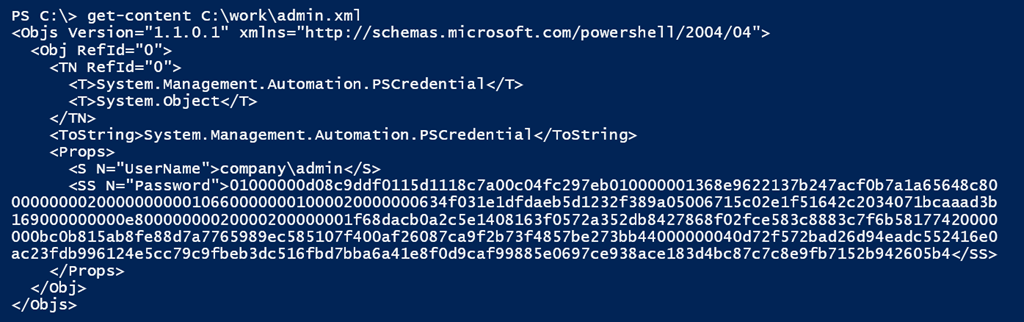
- For credentials that need to be saved to disk, serialize the credential object usingExport-CliXml to protect the password value. The password will be protected as a securestring and will only be accessible to the user who generated the file on the same computer where it was generated.
Powershell Password Security Best Practices App
- For strings that may be sensitive and need to be saved to disk, use ConvertFrom-SecureString to encrypt it into a standard string that can be saved to disk. You can then use ConvertTo-SecureString to convert the encrypted standard string back into a SecureString. NOTE: These commands use the Windows Data Protection API (DPAPI) to encrypt the data, so the encrypted strings can only be decrypted by the same user on the same machine, but there is an option to use AES with a shared key.
